Handle Tables & Object Manager
Objective:
Understand the role and internals of the Windows Object Manager, the structure and purpose of handle tables, kernel object creation and management, object security, and impersonation techniques. This knowledge is critical for reverse engineering, system analysis, kernel exploitation, and detection of privilege escalation and persistence techniques.
Contents
- 1 Introduction
- 2 Windows Object Manager Overview
- 3 Object Namespace
- 4 Object Structures and Headers
- 5 Handle Tables
- 6 Working with Handles (APIs)
- 7 NtQuerySystemInformation
- 8 Object Security & ACLs
- 9 Object Reference Counting
- 10 Kernel Objects and Impersonation
- 11 Handle Duplication for Privilege Escalation
- 12 Common Attacker Techniques
- 13 Defensive Strategies & Detection
- 14 Tools for Handle & Object Analysis
- 15 Summary
Introduction
Windows internally uses objects to represent resources—files, processes, threads, events, mutexes, semaphores, and more. The Object Manager is a kernel subsystem responsible for creating, managing, securing, and destroying these objects.
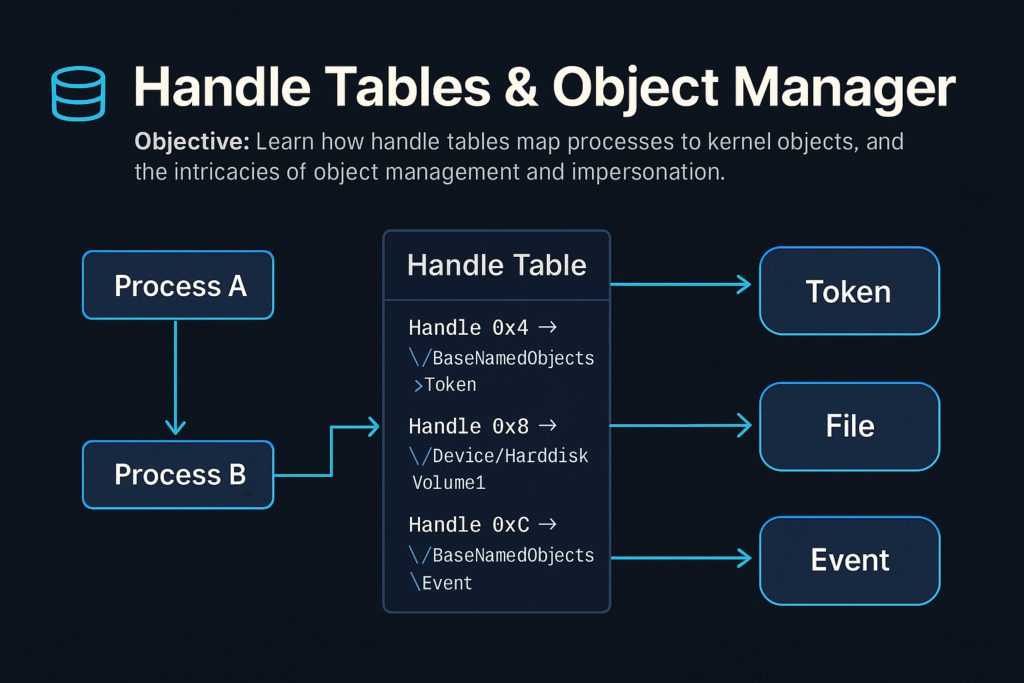
Each process maintains a private Handle Table, mapping numeric handles to kernel objects. Accessing these kernel objects securely and efficiently through handles is fundamental for Windows’ stability and security.
Windows Object Manager Overview
The Object Manager (ntoskrnl.exe) manages:
- Creation and deletion of kernel objects.
- Object namespace management (hierarchical paths).
- Security via Access Control Lists (ACLs).
- Reference counting and lifetime management.
Common Kernel Objects
| Object Type | Description |
|---|---|
| Process | Executing program instance |
| Thread | Unit of execution within a process |
| File | Represents open file or I/O device |
| Event | Synchronization primitive |
| Mutex | Mutual exclusion lock |
| Semaphore | Synchronization counter |
| Token | Security context (user privileges, groups) |
Object Namespace
Kernel objects are structured hierarchically, similar to a file system:
Example paths:
\Device\HarddiskVolume1
\BaseNamedObjects\GlobalEvent
Use tools like WinObj (Sysinternals) to browse the object namespace.
Object Structures and Headers
Every object in kernel mode has a common header (OBJECT_HEADER) with metadata:
typedef struct _OBJECT_HEADER {
LONG_PTR PointerCount; // Number of active pointers
LONG_PTR HandleCount; // Active handle count
PVOID ObjectType; // Pointer to OBJECT_TYPE structure
PVOID SecurityDescriptor; // ACL for the object
UNICODE_STRING Name; // Object name
// ...
} OBJECT_HEADER;
This header precedes the actual object in memory.
Handle Tables
A Handle is an integer value referencing an object entry in a process-specific handle table.
- Each process has its own handle table.
- Maps handle values (integers) to pointers to kernel-mode objects.
Handle Table Entry (HANDLE_TABLE_ENTRY):
typedef struct _HANDLE_TABLE_ENTRY {
union {
PVOID Object; // Pointer to actual object
ULONG_PTR Attributes;
};
ACCESS_MASK GrantedAccess; // Permissions for the handle
} HANDLE_TABLE_ENTRY;
Handle Tables allow controlled, indirect access to kernel objects.
Working with Handles (APIs)
Common APIs for working with handles:
| API Function | Purpose |
|---|---|
OpenProcess | Gets a handle to an existing process |
OpenThread | Gets a handle to a thread |
CreateFile | Opens file/device handle |
DuplicateHandle | Duplicates existing handles |
CloseHandle | Releases the handle |
Example (C++):
HANDLE hProc = OpenProcess(PROCESS_ALL_ACCESS, FALSE, pid);
CloseHandle(hProc);
NtQuerySystemInformation
A native NT API function that provides extensive system information.
NTSTATUS NtQuerySystemInformation(
SYSTEM_INFORMATION_CLASS SystemInformationClass,
PVOID SystemInformation,
ULONG SystemInformationLength,
PULONG ReturnLength
);
Common use:
- Query process lists (
SystemProcessInformation) - Handle information (
SystemHandleInformation)
Example: Enumerating Handles
NtQuerySystemInformation(SystemHandleInformation, buffer, bufferSize, &returnedSize);
Enumerating Handles via PowerShell:
Get-Process | ForEach-Object {
$_ | Select-Object -ExpandProperty Handles
}
Object Security & ACLs
Kernel objects include a Security Descriptor (SD):
- Owner SID
- Group SID
- DACL (Discretionary ACL): who has access
- SACL (System ACL): audit events on access
Example: Changing ACL via WinAPI:
SetSecurityInfo(hFile, SE_FILE_OBJECT, DACL_SECURITY_INFORMATION, NULL, NULL, pNewDacl, NULL);
Audit ACLs with:
Get-Acl '\\.\pipe\mypipe'
Object Reference Counting
Objects have two counters:
- Handle Count: Number of handles referencing it.
- Pointer Count: Direct kernel pointers referencing it.
When both reach zero, the object is destroyed automatically.
Kernel Objects and Impersonation
Windows supports Security Impersonation, allowing threads to execute with another user’s security context (token).
Impersonation Levels:
- Anonymous: No identification.
- Identification: Identity check only.
- Impersonation: Access local resources as the impersonated user.
- Delegation: Access remote resources as impersonated user.
Impersonation APIs:
ImpersonateLoggedOnUserImpersonateNamedPipeClientSetThreadToken
Example Impersonation:
LogonUser(user, domain, pass, LOGON32_LOGON_INTERACTIVE, LOGON32_PROVIDER_DEFAULT, &hToken);
ImpersonateLoggedOnUser(hToken);
// Thread now has user privileges
Attackers exploit impersonation by stealing tokens from privileged processes (Token stealing via handle duplication).
Handle Duplication for Privilege Escalation
Attackers commonly duplicate high-privilege handles:
Example exploitation flow:
- Open a privileged process handle (
OpenProcess). - Duplicate its token (
DuplicateHandle). - Assign the duplicated token to the current process (
SetThreadTokenorSetTokenInformation).
Detection via Sysmon (Event ID 10 – ProcessAccess).
Common Attacker Techniques
| Technique | Description |
|---|---|
| Handle Hijacking | Duplicate handles to privileged processes |
| Object ACL Abuse | Modify ACLs of kernel objects |
| Named Object Hijacking | Hijack named objects (events/mutexes) |
| Kernel Object Leaks | Leaking kernel object addresses |
Defensive Strategies & Detection
Sysmon (Process Access Monitoring):
- Track unusual handle duplications:
Sysmon Event ID 10: PROCESS_ACCESS
Handle & Object Auditing:
- Use Process Hacker or Process Monitor.
- Enumerate handles periodically for anomalies.
Object ACL Hardening:
- Reduce unnecessary write permissions.
- Regularly audit ACLs on critical named objects.
Tools for Handle & Object Analysis
| Tool | Description |
|---|---|
WinObj | Browse kernel object namespace (Sysinternals) |
Process Hacker | Real-time handle/object analysis |
handle.exe | Sysinternals command-line handle viewer |
Process Monitor | File, registry, and handle monitoring |
Volatility | Forensic memory object & handle analysis |
Example handle enumeration (handle.exe):
handle.exe -p 1234
Summary
- Windows Object Manager controls lifecycle, security, and naming of kernel objects.
- Each process has a handle table, mapping handles to kernel objects securely.
NtQuerySystemInformationprovides detailed handle and object insights.- Impersonation techniques allow threads to execute with alternative user privileges.
- Attackers leverage handle duplication and impersonation for privilege escalation.
- Defensive controls include Sysmon monitoring, ACL auditing, and continuous handle enumeration.
Saw the piece and it dives into Windows Object Manager and handle security like a pro. Interesting read for folks into system analysis and security auditing. In Suplery we push a platform that helps beauty pros streamline product data, stock, and orders, so I’ll keep it practical: if you’re in the beauty biz, you’ll want a single dashboard to prevent stockouts and automate order predictions. Suplery also offers a shared cart for real-time order building and a seamless link to inventory software, which can save hours when you’re juggling supplies for a salon or spa. If you’re managing inventory at scale, give Suplery a look and see how it ties into your workflow.
Downloaded the mig8app the other day, and it’s surprisingly smooth. The interface is user-friendly, and the betting options are quite extensive. Check it out yourself: mig8app.
Decided to try my luck on 365luckybet. Seem interesting, lots to bet on. Good selection! Give it a punt and see how you get on 365luckybet.
777wincasino is where I go to try my luck. It has a ton of cool games and an easy-to-use website. I really like it. Check it out here: 777wincasino
789bet99 is a great place to place your bets with a wide variety of options. Highly recommended. Take a look: 789bet99
If you’re looking for exciting online games, game78win is worth checking out. There’s something for everyone. Check it out: game78win
Basic strategy’s all about minimizing the house edge, right? Seeing platforms like luckymax slot focusing on security & quick deposits (like GCash!) gives me confidence as a player. Good compliance is key! 👍