Windows Registry Internals
Objective: Explore the internal structure and functionality of the Windows Registry, including its hive-based architecture, key-value model, data types, and how it enables system configuration. Understand how attackers leverage registry paths such as
Runkeys for persistence, and how defenders can detect and investigate these techniques.
Contents
- 1 Introduction
- 2 Registry Architecture Overview
- 3 Core Registry Hives
- 4 Registry File Locations
- 5 Keys, Values, and Data Types
- 6 Registry Pathing
- 7 Run Key Persistence
- 8 Other Registry Persistence Locations
- 9 Registry Backup and Restore
- 10 Registry Permissions and ACLs
- 11 Red Team & Malware Use Cases
- 12 Registry Forensics
- 13 Summary
Introduction
The Windows Registry is a centralized, hierarchical database used by the Windows operating system and many applications for configuration and operational data.
It stores everything from hardware driver configs, installed software settings, user preferences, and system boot configuration to startup execution paths, which makes it an attractive target for attackers seeking persistence and privilege escalation.
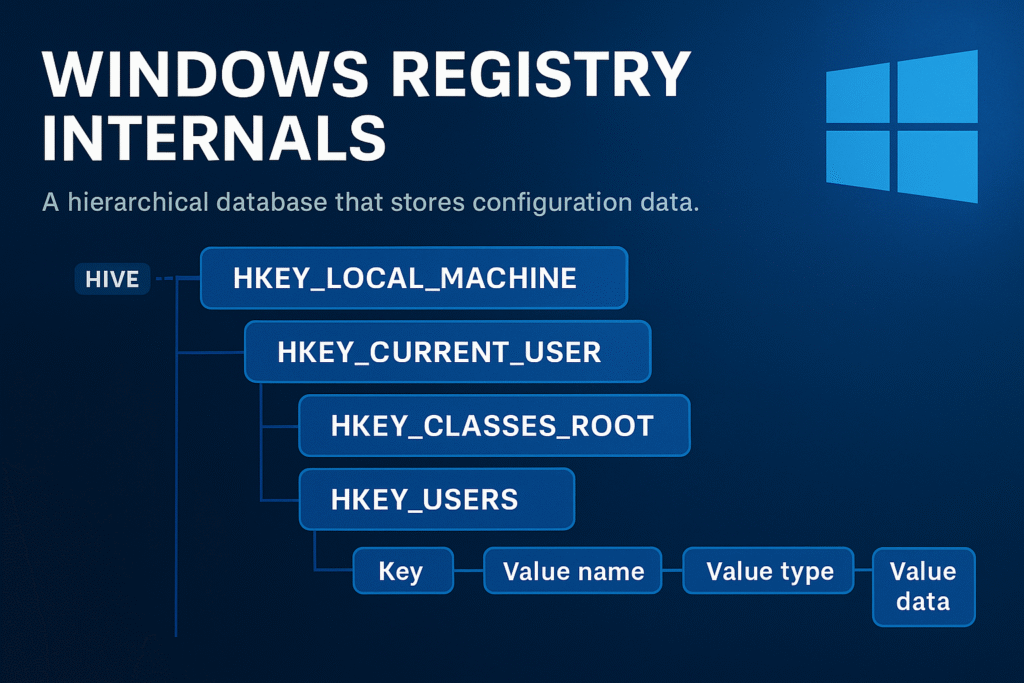
Registry Architecture Overview
The Windows Registry is structured like a file system:
- Keys = Folders
- Values = Files
- Hives = Root-level logical divisions (backed by real files)
The Registry is accessible via:
- Registry Editor (
regedit.exe) - API calls like
RegOpenKeyEx,RegQueryValueEx,RegSetValueEx - Command-line tools (
reg.exe,powershell,regedit,wmic)
Core Registry Hives
Each hive maps to a physical file on disk. Hives are loaded into memory during system boot or user login.
Major Root Hives
| Hive | Description | Backing File |
|---|---|---|
HKEY_LOCAL_MACHINE (HKLM) | Machine-wide configuration | SYSTEM, SOFTWARE, etc. |
HKEY_CURRENT_USER (HKCU) | Current logged-in user’s settings | NTUSER.DAT |
HKEY_CLASSES_ROOT (HKCR) | File extension and COM associations | Alias of HKLM\Software\Classes and HKCU\Software\Classes |
HKEY_USERS (HKU) | All user profiles loaded | Includes SID-named keys |
HKEY_CURRENT_CONFIG (HKCC) | Dynamic hardware profile data | Derived from HKLM\SYSTEM |
Registry File Locations
| File | Purpose | Path |
|---|---|---|
SYSTEM | Kernel drivers, boot info | %SystemRoot%\System32\Config\SYSTEM |
SOFTWARE | Installed programs, OS settings | %SystemRoot%\System32\Config\SOFTWARE |
SECURITY | Local security policies | %SystemRoot%\System32\Config\SECURITY |
SAM | Local user/password database | %SystemRoot%\System32\Config\SAM |
NTUSER.DAT | Current user settings | %UserProfile%\NTUSER.DAT |
These files are locked during runtime and can be accessed offline using tools like FTK Imager or Registry Explorer.
Keys, Values, and Data Types
Keys
A key is similar to a directory and can contain:
- Subkeys
- Values
- A default unnamed value
Values
Each key can contain one or more values, which consist of:
- Name
- Data Type
- Data
Registry Data Types
| Type | Symbol | Description |
|---|---|---|
REG_SZ | String | Plain text string |
REG_EXPAND_SZ | Expandable string | Supports environment variables |
REG_DWORD | 32-bit number | Often used for flags/settings |
REG_QWORD | 64-bit number | Used in newer configurations |
REG_BINARY | Binary data | Raw hex, often device configurations |
REG_MULTI_SZ | Multi-string | Array of strings, null-delimited |
Registry Pathing
Registry paths are expressed like filesystem paths:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion
PowerShell can be used to browse and interact with registry keys as if they are drives:
cd HKLM:\SOFTWARE\Microsoft\Windows
Get-ItemProperty .
Run Key Persistence
One of the most abused persistence techniques is via the Run or RunOnce registry keys.
Common Run Key Paths
| Location | Description |
|---|---|
HKLM\Software\Microsoft\Windows\CurrentVersion\Run | Runs for all users at boot |
HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce | Runs only once for all users |
HKCU\Software\Microsoft\Windows\CurrentVersion\Run | Runs at login for the current user |
HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce | Runs only once for current user |
Example (Manual Persistence)
Set-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\Run" `
-Name "Updater" `
-Value "C:\Users\Public\updater.exe"
This would launch updater.exe at user logon.
Detection Tip:
- Use
Autorunsfrom Sysinternals or check registry directly:
Get-ItemProperty 'HKCU:\Software\Microsoft\Windows\CurrentVersion\Run'
Other Registry Persistence Locations
| Key | Purpose |
|---|---|
HKLM\Software\Microsoft\Active Setup\Installed Components | Used by IE and apps to auto-start on login |
HKLM\SYSTEM\CurrentControlSet\Services | Create a persistent service |
HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit | Modify login initialization |
HKLM\Software\Microsoft\Windows\CurrentVersion\ShellServiceObjectDelayLoad | Delayed loading COM object |
HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows\load | Legacy autorun vector |
HKLM\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Run | Persistence in 32-bit view on 64-bit system |
Registry Backup and Restore
Backup entire hives with:
reg export HKLM\Software software_backup.reg
Restore with:
reg import software_backup.reg
For forensics, extract registry hives offline and analyze them using:
- Registry Explorer
- Eric Zimmerman’s RECmd
- FTK Imager
- Autopsy or Volatility plugins for memory dumps
Registry Permissions and ACLs
Each key has its own ACL (Access Control List), viewable with:
(Get-Acl 'HKLM:\Software\Microsoft\Windows').Access
Tools like SetACL, PowerShell, or psexec can be used to escalate via insecure permissions (e.g., attacker can write to a privileged run key).
Red Team & Malware Use Cases
| Technique | Abuse |
|---|---|
| Startup Execution | Run keys, RunOnce, ActiveSetup |
| Service Hijacking | Modify ImagePath under Services |
| Userinit/Login | Append malicious payload to Userinit or Shell |
| COM Hijack | Register fake COM object in HKCR\CLSID |
| AV Evasion | Hide payload in registry as base64 or encrypted blob under benign key, decode in memory |
Example of storing payload as encoded string:
Set-ItemProperty -Path "HKCU:\Software\Microsoft\Something" -Name "Config" -Value ([Convert]::ToBase64String([IO.File]::ReadAllBytes("payload.dll")))
Registry Forensics
For DFIR analysts, registry artifacts can indicate:
- Malware persistence
- User activity (recent files, typed paths)
- USB device history (
SYSTEM\CurrentControlSet\Enum\USBSTOR) - Program execution evidence (e.g.,
UserAssist,ShimCache) - MRU (Most Recently Used) lists
Recommended Tools:
- Eric Zimmerman’s Registry Explorer + RECmd
- NirSoft tools (ShellBagsView, USBDeview, etc.)
- Velociraptor for live enterprise-wide registry search
Summary
- The Windows Registry is a core part of system configuration and operation.
- It uses hives, keys, values, and types to store structured data.
- Persistence via
Runkeys is trivial and highly common. - Powerful red team techniques involve modifying service, COM, or logon keys.
- Defensive tools can monitor or lock registry keys to prevent abuse.
Alright, listen up: dangkysv388 is where it’s at if you’re serious. The registration process was a breeze, and I was playing in minutes. Definitely worth a shot. You gotta try dangkysv388
sv88top seems like a promising platform. Fair and reliable site. I am having a good experience. You can try it. sv88top
Alright, looking into Linkred88. Easy access? Yes! Good options? Double Yes! Go have some fun: linkred88
Alright mates, Win88blueslot is the spot for a decent flutter. I’ve had a few good spins there. Give win88blueslot a go, yeah?
Looking to dive into some cockfighting action? Sv388 Login Juraganslot’s got ya covered. Just signed up and it’s pretty straightforward. Check out sv388 login juraganslot.
Time to give 88jllogin a shot. Hoping for a smooth login experience and some winning streaks. Let’s see what it’s all about! Try your luck 88jllogin
Logging in to ph987login is usually a breeze. Occasionally, it gives me trouble, but it’s generally reliable. Just keep that in mind.
Another 639jl login portal folks, this one works fine! Saves the hassle of digging through the main site to find the right page. One click and you’re in!. Try it: 639jllogin
Love the breakdown-it’s like having a pro at the table. For those looking to level up, check out the AI-driven insights at JiliOK Link. A fresh take on strategy and fun.
DPbosslogin seems pretty slick for what it is. If you know, you know, right? Easy to navigate, and gets the job done. Don’t say I sent you but give it a try: dpbosslogin
Trirangagame – the logo has a certain something. What do you guys think of their slots and table games offerings? Any recommendations? Give it a go: trirangagame
Jljl99applogin – Looks new – Anyone checked out the jljl99applogin app? Is it user-friendly? And is it worth downloading? Your thoughts will be welcome! Begin to play at: jljl99applogin
Excellent breakdown of registry persistence mechanisms! The Run keys analysis is particularly valuable for threat hunters. Similar to how online platforms like queen ph legit maintain secure transaction logs, monitoring registry changes provides crucial forensic evidence. The hive-based architecture explanation helps defenders understand attack surface boundaries. Great primer for SOC analysts!
Interesting points about bankroll management & RTP! Seeing platforms like lucky play casino casino prioritize things like GCash & fast registration (under 90 secs!) is smart for the Philippine market. Good analysis!