Windows File System Internals (NTFS)
Objective: The NTFS (New Technology File System) is the default file system for modern Windows versions, designed to be secure, scalable, recoverable, and rich in metadata support.
Contents
- 1 Overview
- 2 Key NTFS Features
- 3 The Master File Table (MFT)
- 4 File Record Attributes
- 5 File Metadata and Timestamps
- 6 Alternate Data Streams (ADS)
- 7 Directory Structure & Indexing
- 8 Journaling with $LogFile
- 9 NTFS Recovery Concepts
- 10 USN Journal (Change Journal)
- 11 NTFS Object IDs & Reparse Points
- 12 Common NTFS Attacks and Abuses
- 13 Low-Level Tools for NTFS Exploration
- 14 Summary
Overview
The NTFS (New Technology File System) is the default file system for modern Windows versions, designed to be secure, scalable, recoverable, and rich in metadata support. Unlike FAT32 or exFAT, NTFS introduces complex data structures, a journaled metadata system, access control lists (ACLs), hard/soft links, and alternate data streams (ADS).
Key NTFS Features
| Feature | Description |
|---|---|
| Metadata-driven | Every file and directory is stored as a metadata record in the MFT |
| Journaling | Changes to critical metadata are recorded in the $LogFile before being committed |
| Security | Full support for file permissions, ACLs, and encryption (EFS) |
| ADS (Alternate Data Streams) | Allows multiple data streams per file |
| Compression & Encryption | Built-in per-file compression and support for EFS |
| Hard Links & Reparse Points | Advanced linking and symbolic path redirection features |
| Sparse Files | Support for efficiently handling large files with empty regions |
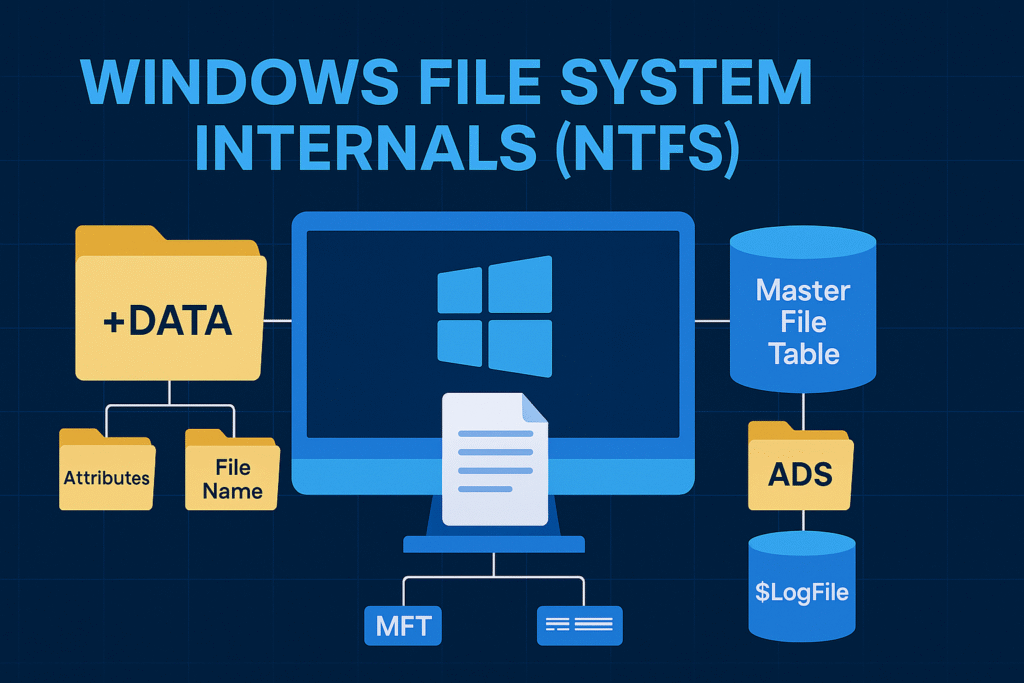
The Master File Table (MFT)
At the heart of NTFS is the MFT (Master File Table). Think of it as the central database of the entire file system. Every file, folder, and metadata structure is stored as an MFT record, including internal system files.
MFT Layout
Each record in the MFT is 1024 bytes and contains:
- File metadata (timestamps, size, attributes)
- Pointers to the file’s data blocks (runs)
- Named streams (e.g.,
::$DATA) - File name entries (long and short names)
Key System Files in the MFT
| Entry Name | Purpose |
|---|---|
$MFT | The Master File Table itself |
$Bitmap | Tracks which clusters are used/free |
$LogFile | Journals metadata changes |
$Secure | Security descriptors and ACLs |
$Volume | Volume info (version, dirty flag) |
$AttrDef | List of valid attributes |
$Extend | Houses extended features (like quotas, EFS, USN Journal) |
File Record Attributes
Each NTFS file has a set of attributes that describe both the file and its contents. Attributes are stored either resident (inside the MFT entry) or non-resident (stored in separate clusters).
Common Attributes:
| Attribute | Description |
|---|---|
STANDARD_INFORMATION | Basic timestamps and permission flags |
FILE_NAME | Long and short name entries |
DATA | The file’s actual data (can be named streams) |
OBJECT_ID | Unique identifier for tracking |
SECURITY_DESCRIPTOR | NTFS ACLs |
ATTRIBUTE_LIST | Used if the record can’t fit in one MFT entry |
Resident Data
- Small files (<700 bytes) are stored directly in the MFT.
Non-Resident Data
- Larger files are stored elsewhere on disk and referenced via “data runs”.
File Metadata and Timestamps
NTFS tracks multiple timestamps:
Created: File creation timeModified: Last content modificationMFT Changed: When metadata was last changedAccessed: Last file access time
These are stored in STANDARD_INFORMATION and FILE_NAME attributes. Tools like MFTECmd or FTK Imager extract these for forensic timelines.
Alternate Data Streams (ADS)
NTFS supports multiple unnamed or named data streams in a single file. The main stream is usually :$DATA, but you can add hidden ones.
Example:
echo "secret" > notepad.txt:hidden
type notepad.txt:hidden
Forensics Concern:
- ADS are often used to hide payloads or staging binaries.
dir /Rwill list streams in Windows.
Directory Structure & Indexing
NTFS directories are files themselves with INDEX_ROOT and INDEX_ALLOCATION attributes.
- Small directories store entries directly inside the MFT (
INDEX_ROOT) - Large directories spill over to other clusters (
INDEX_ALLOCATION)
This design allows binary search indexing (B-tree like) instead of linear scanning.
Journaling with $LogFile
NTFS is a journaling file system.
$LogFilestores redo/undo logs for critical metadata changes.- Ensures metadata integrity after a power failure or crash.
- Does not journal actual file content, only structural data.
This mechanism supports transactional consistency for files.
NTFS Recovery Concepts
NTFS uses a few safety mechanisms:
- $LogFile Recovery
- Replay undo/redo entries post-crash
- CHKDSK
- Scans metadata for inconsistencies
- Can fix MFT, indexes, bitmap mismatches
- Volume Dirty Bit
- Flag inside
$Volumethat triggers auto-CHKDSK
- Flag inside
USN Journal (Change Journal)
Located in: $Extend\$UsnJrnl
- Tracks all file-level changes (created, renamed, modified, deleted)
- Used by tools like antivirus, backup software, and forensic tools
- Each event is indexed by USN ID and timestamp
Enable / Query USN Journal:
fsutil usn queryjournal C:
NTFS Object IDs & Reparse Points
- Object IDs: Unique GUIDs for file tracking
- Reparse Points: Used for symbolic links, junctions, OneDrive placeholders
Types of reparse tags:
IO_REPARSE_TAG_SYMLINK– Symbolic linkIO_REPARSE_TAG_MOUNT_POINT– JunctionIO_REPARSE_TAG_APPEXECLINK– App execution alias
You can create symbolic links using:
mklink file2.txt file1.txt
Common NTFS Attacks and Abuses
| Abuse Technique | Description |
|---|---|
| ADS Persistence | Hide malicious DLLs or scripts in alternate streams |
| MFT Record Abuse | Create thousands of MFT entries to trigger slowdowns or detection blind spots |
| Symbolic Link Hijack | Abuse reparse points to redirect execution |
| USN Journal Wipe | Delete forensic history using low-level tools |
Low-Level Tools for NTFS Exploration
| Tool | Purpose |
|---|---|
NTFSInfo (Sysinternals) | View cluster sizes, MFT layout |
MFTECmd (Eric Zimmerman) | Parse MFT and timestamps |
FTK Imager | Browse NTFS structure for forensics |
fsutil | Query volume, reparse points, streams |
NTFSWalker | Inspect MFT and attributes |
WinHex / 010 Editor | View raw disk sectors and parse binary templates |
Summary
- NTFS is a highly advanced file system that embeds metadata, journaling, and fine-grained security into every file.
- The MFT is the backbone of the file system, storing every file and folder as a database-like entry.
- ADS, USN, and Reparse Points introduce both powerful features and potential attack surfaces.
- NTFS journaling (
$LogFile) and recovery structures provide strong integrity guarantees.
That’s a great point about building skills, not just relying on luck! It reminds me of resources like jiliok login, which focuses on education within the iGaming space – a smart approach for new players! Really helps with responsible gaming.
Interesting analysis! Understanding game mechanics is key, and platforms like ph978 casino are evolving to help with that. Strategic play really elevates the experience, don’t you think? It’s about more than just luck!
Fala galera do bolão! A apostaganha4 parece ter umas apostas interessantes. Preciso dar uma olhada com mais calma, mas a primeira impressão foi boa. Quem sabe a gente não faz uns gains por lá? Confere aí: apostaganha4
Yo what’s up, heard some good things from the homies about tk88bet. Gonna check them out myself. They said the odds are good and customer service is on point. Fingers crossed I win big! Definitely gonna try tk88bet out!
Bk8vietnam is my go-to spot for online betting. Always a smooth experience and great promotions. Check it out here: bk8vietnam
Finding a reliable BK8 link can be a pain. Thankfully, bk8link1.info has got you covered. Easy to find the latest access. Give it a look: bk8link1
Feeling lucky? Iwinfortune might be your next favorite spot. They have a lot of games and the site is really user-friendly. See for yourself: iwinfortune
Jilipark2 is fun! Fast payouts and great customer service. I had a withdrawal issue but they fixed it really fast. It’s my favorite! jilipark2
Gotta say, 123dbet caught my eye. Gave it a whirl, and I’m impressed! Cool interface. Defo worth a look-see! 123dbet
Okay, 55bmwslot… fingers crossed for some smooth spins and big payouts! Let’s see what those reels can do! Give them a try now 55bmwslot