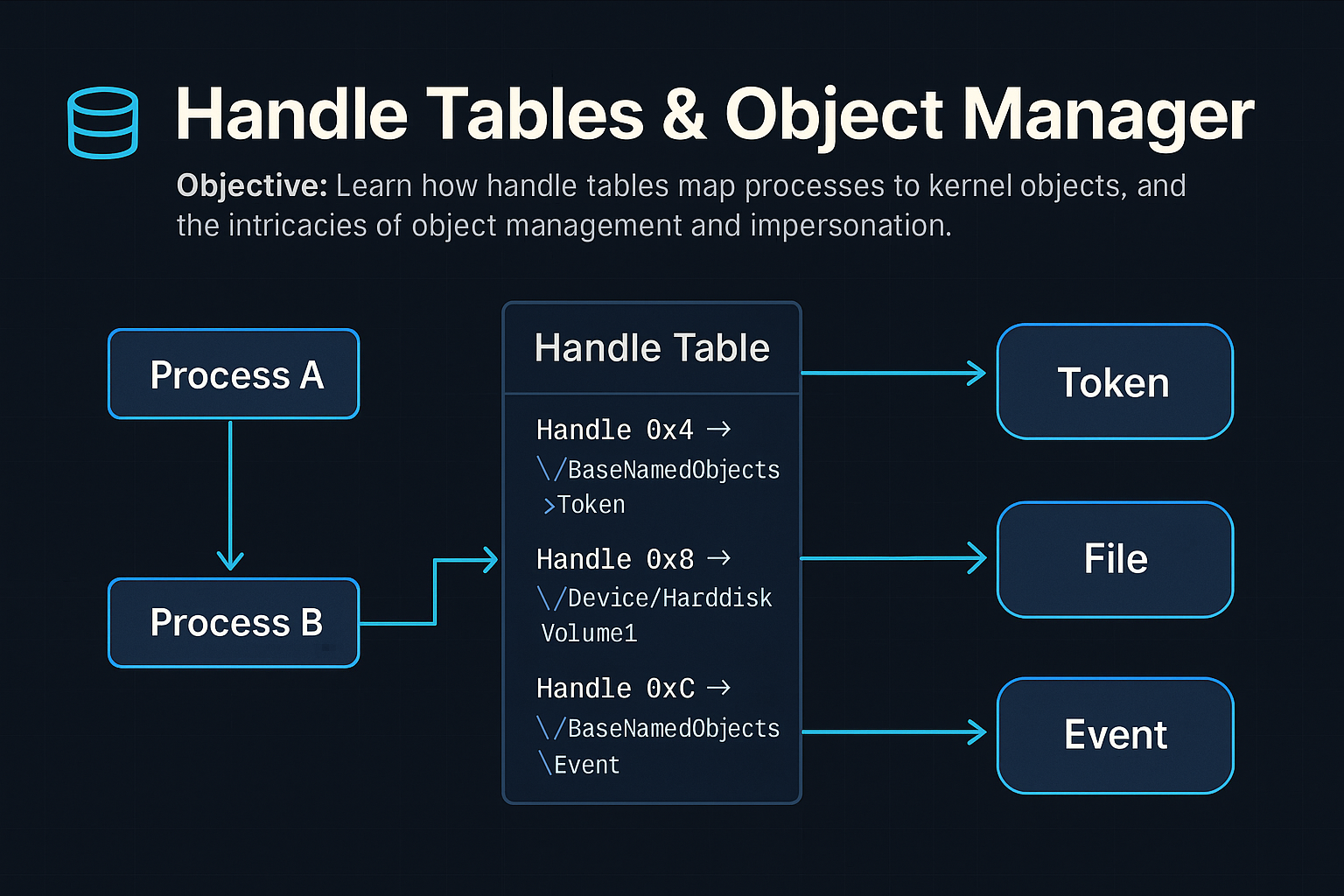
Understand the role and internals of the Windows Object Manager, the structure and purpose of handle tables, kernel object…
Tutorials
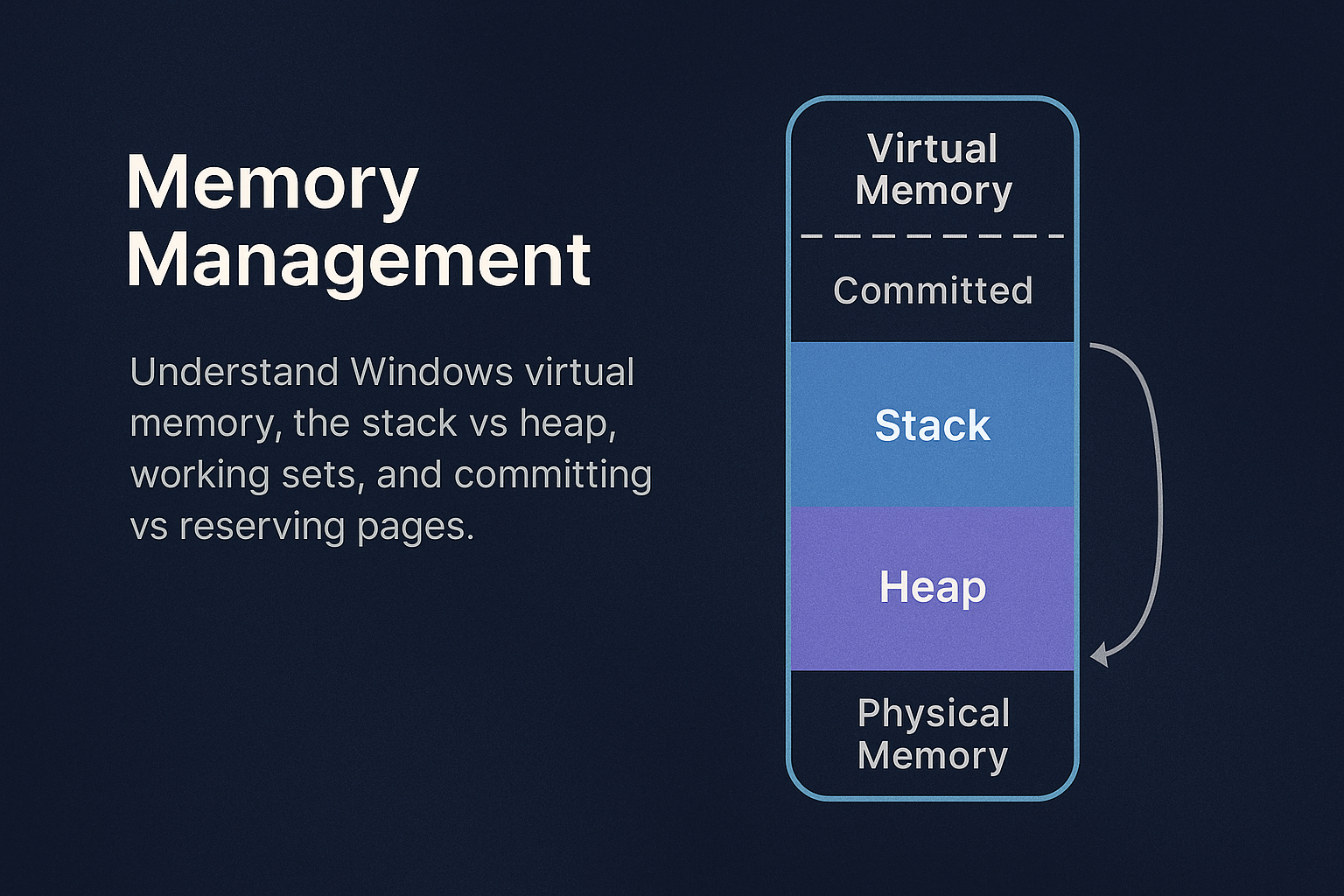
Understand the internal architecture and functionality of Windows memory management, including virtual memory, physical memory mappings, distinctions between stack…
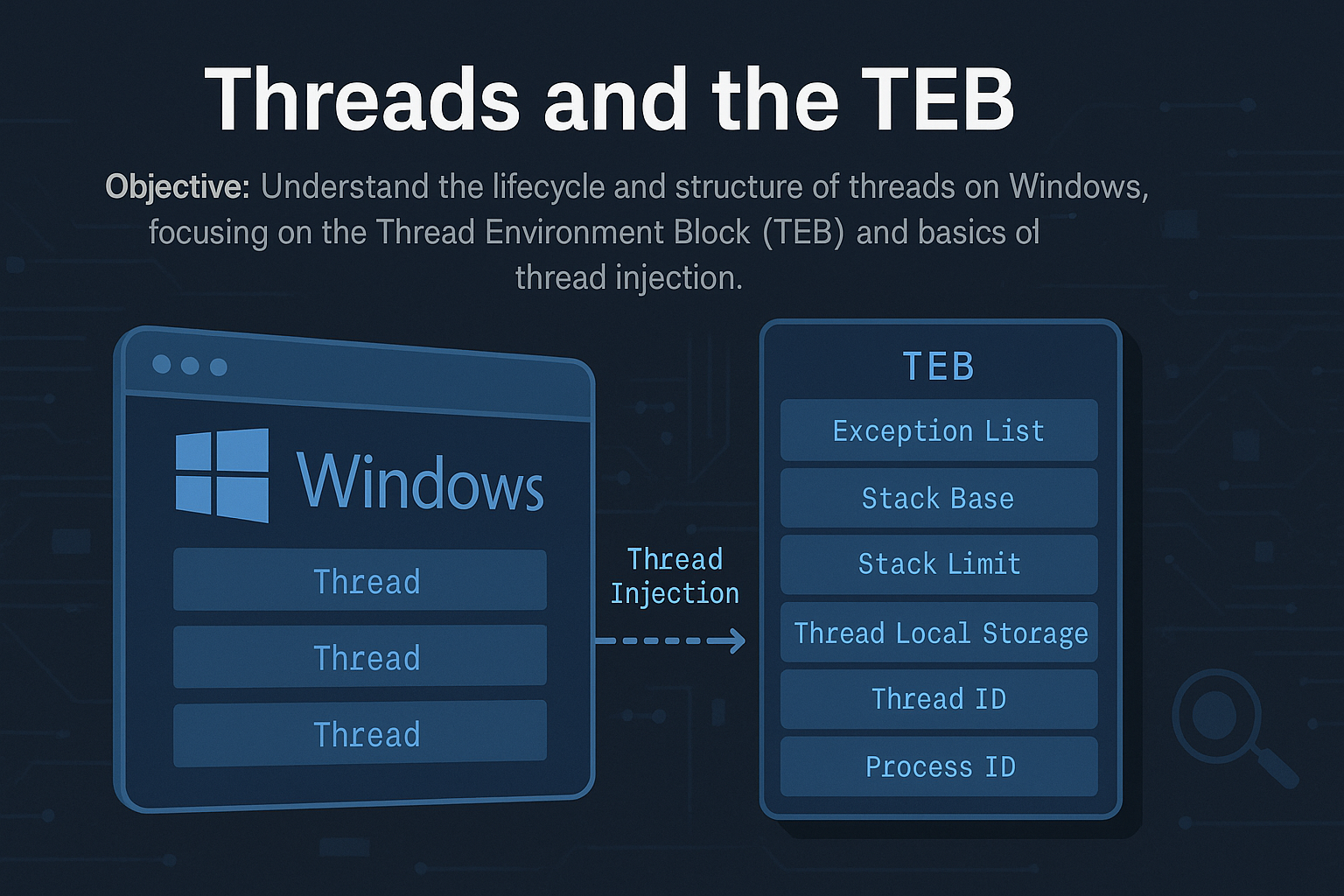
Understand the internal workings of threads on Windows, the lifecycle of a thread from creation to termination, the critical…
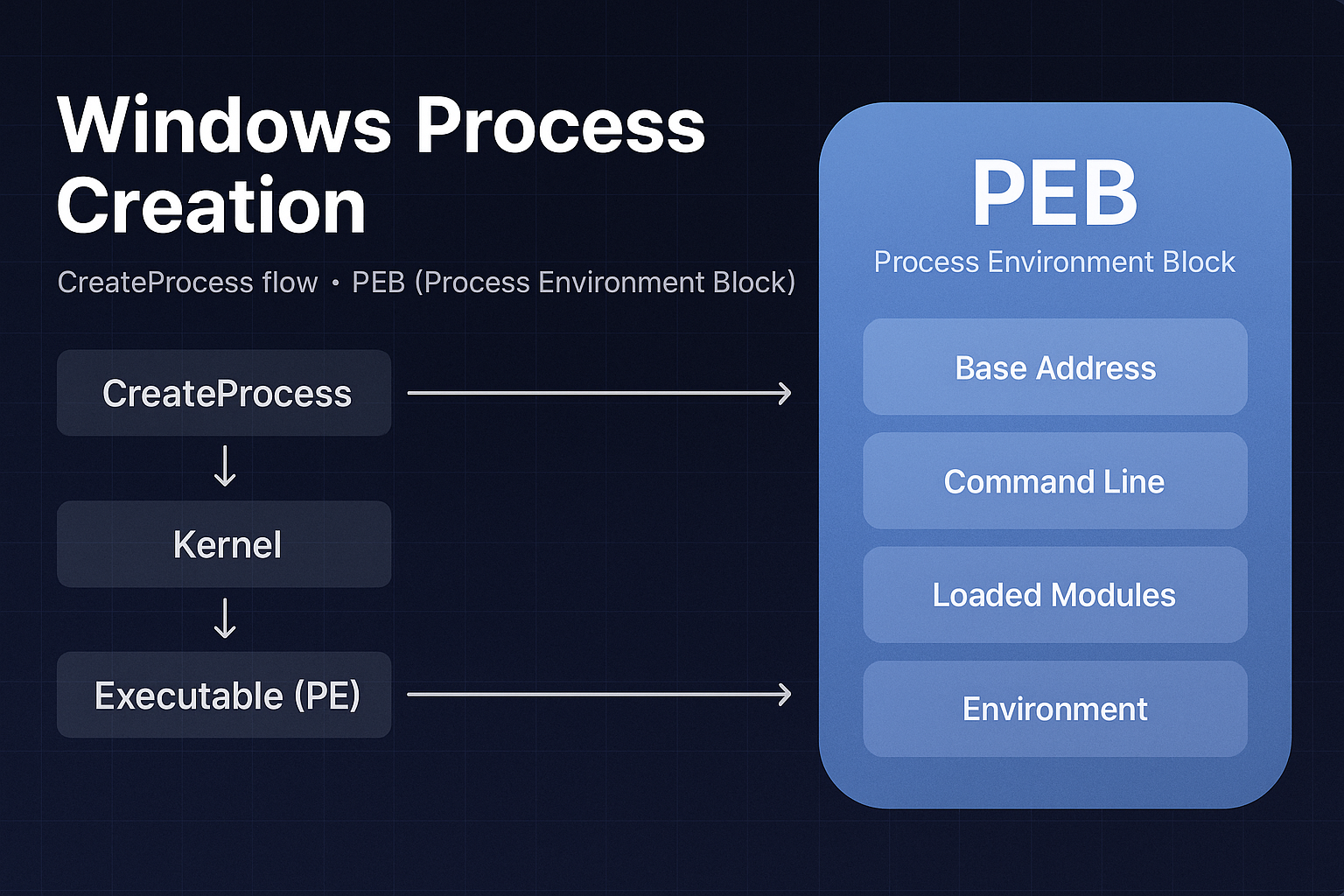
Deeply understand how Windows creates new processes, detailing the internal workings of the CreateProcess API, kernel object management, memory…
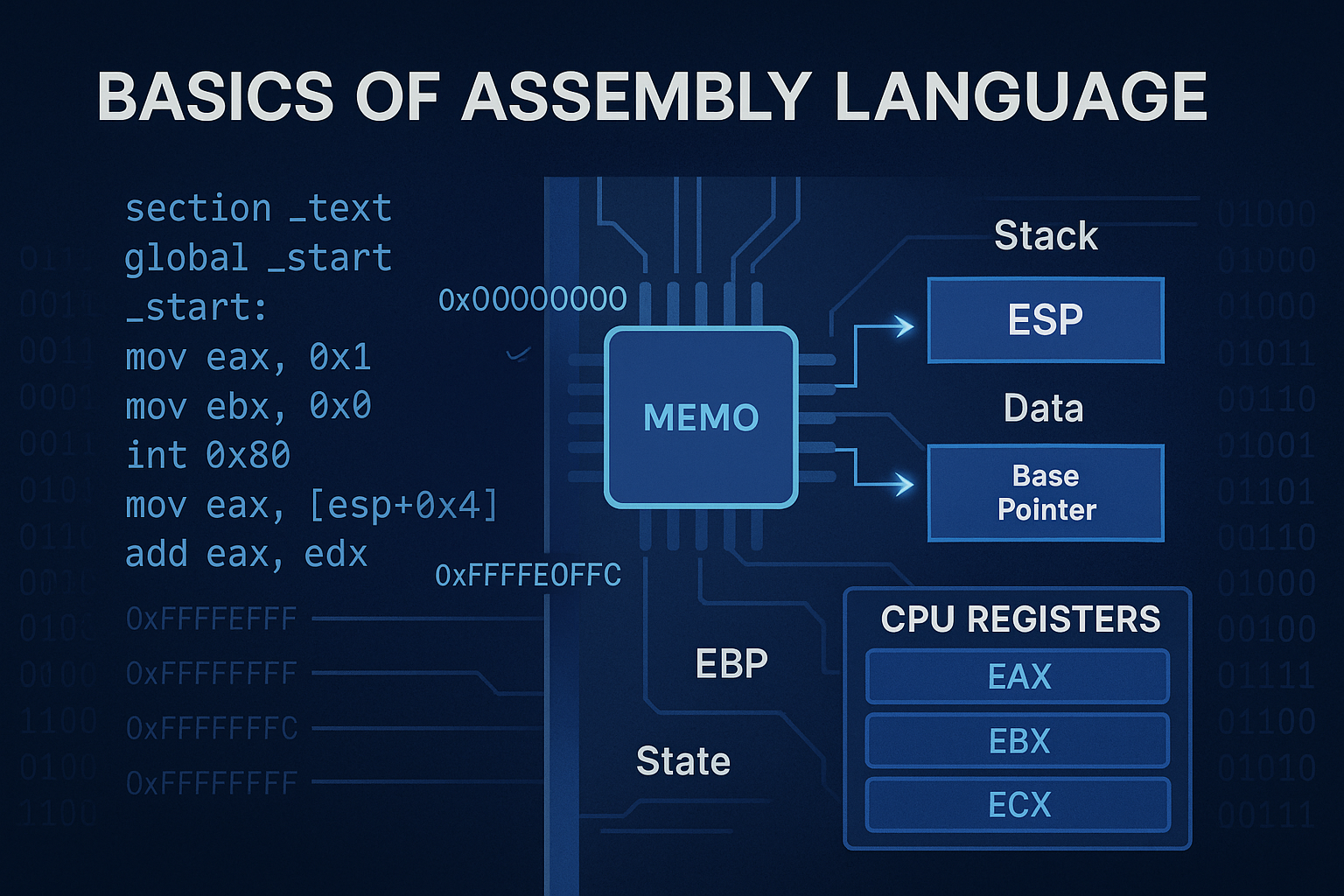
To gain a deep, foundational understanding of how x86 and x64 assembly work, from CPU registers and calling conventions…
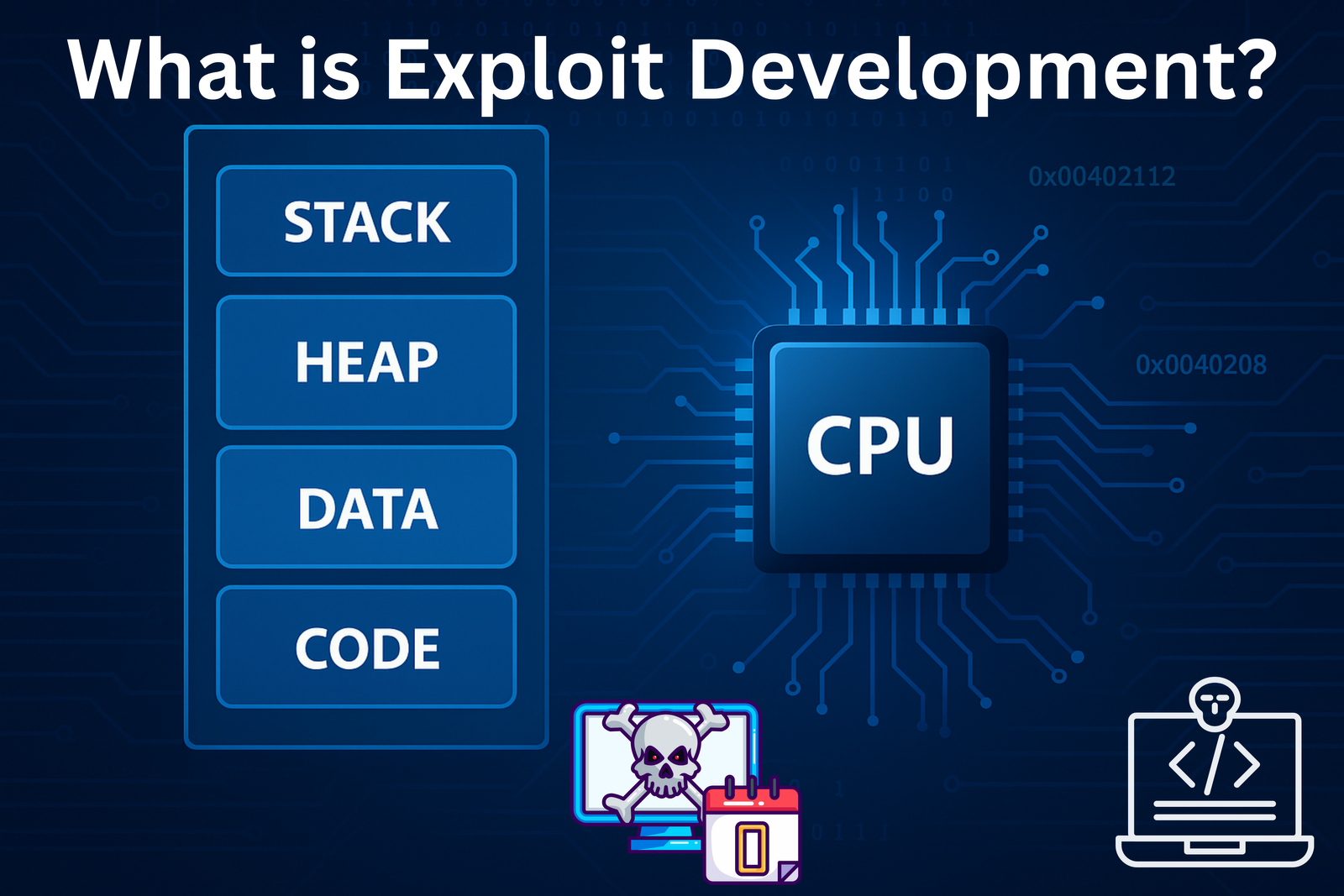
To build a comprehensive understanding of what exploit development is, its goals, classifications, and how attackers leverage vulnerabilities to…
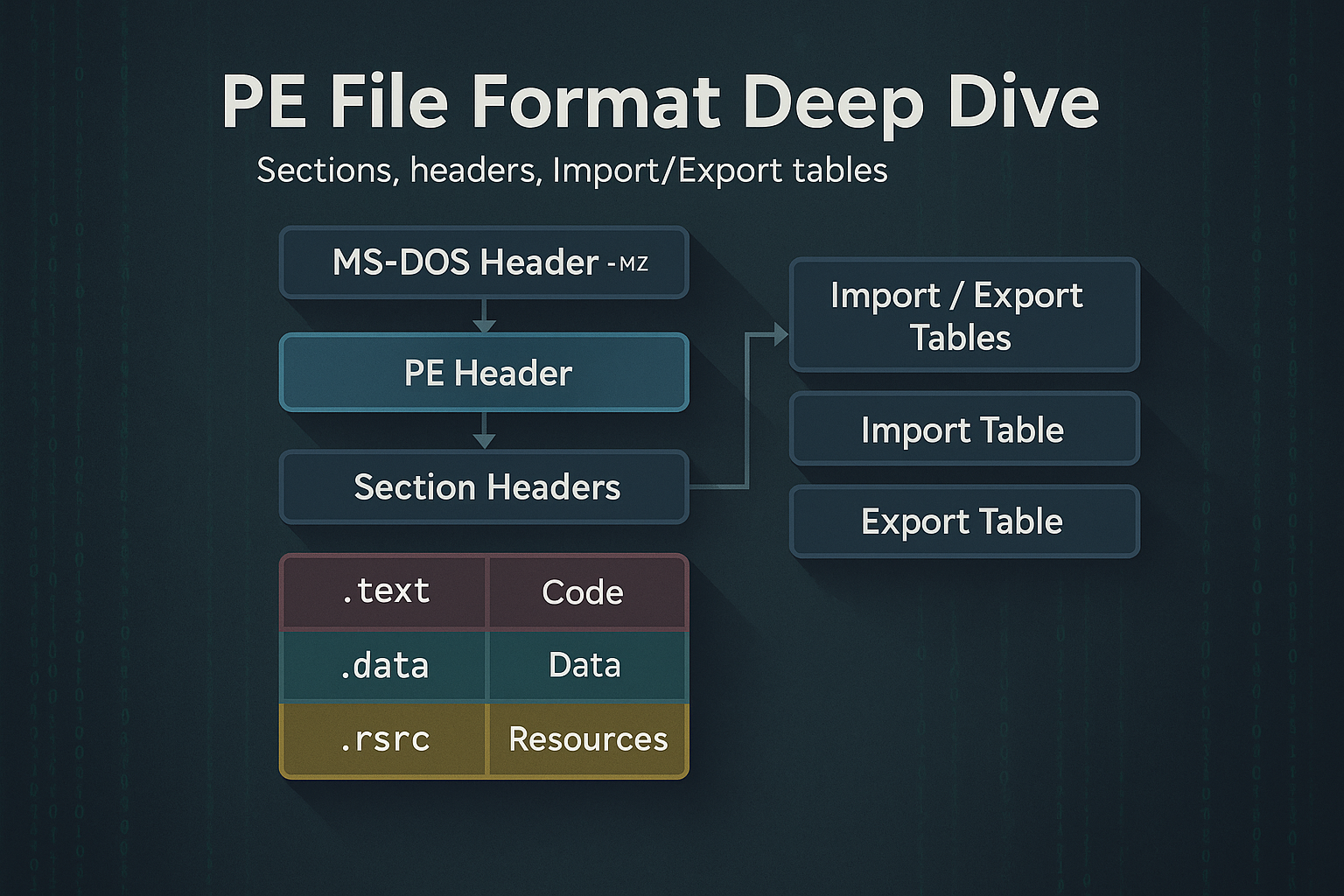
Understand the internal structure of Windows Portable Executable (PE) files, including the DOS and NT headers, section table, and…
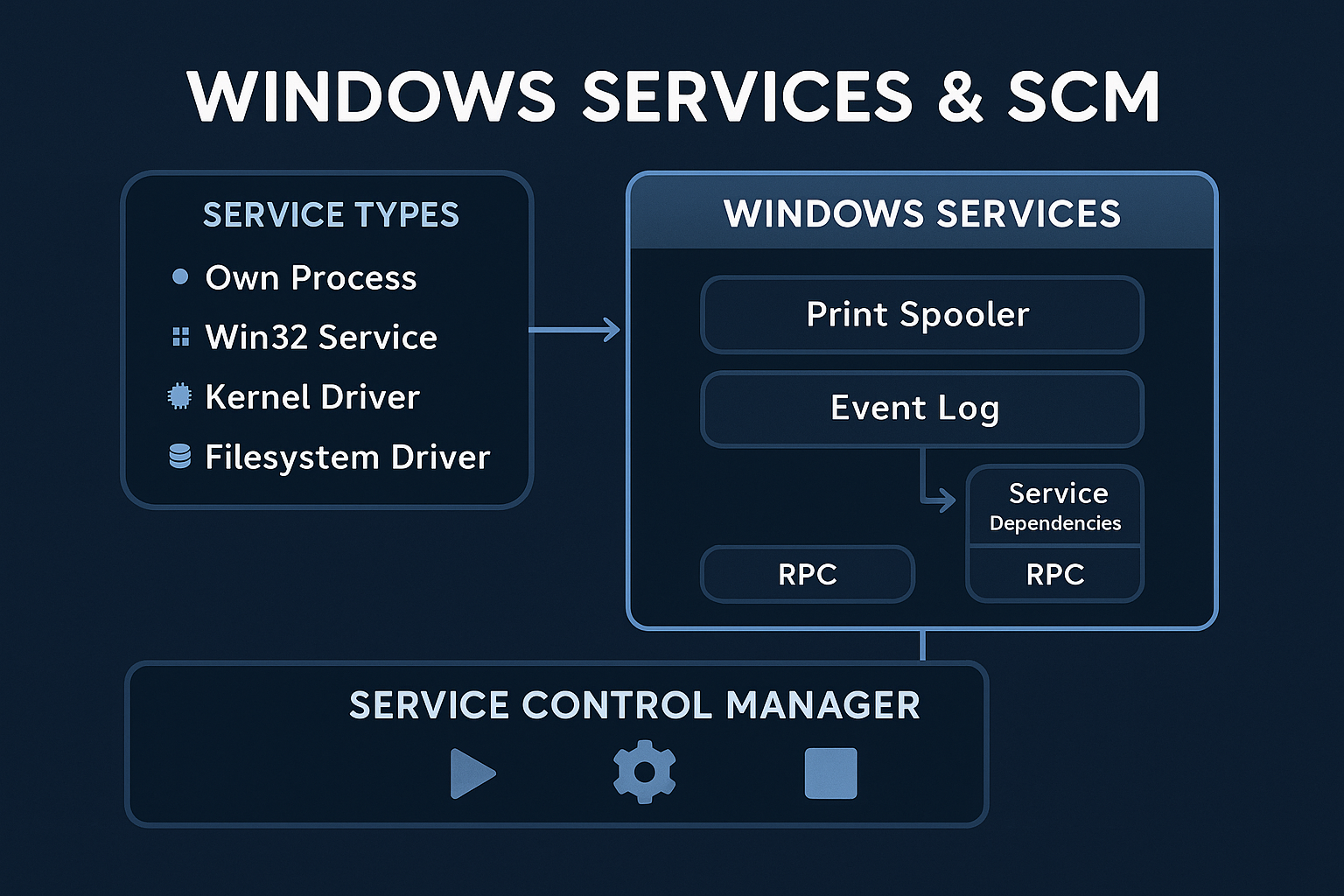
Understand the architecture and functioning of Windows services, how the Service Control Manager (SCM) manages service lifecycles, service types,…